Introduction: An Elusive Shadow in the World of Online Advertising
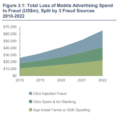
In the digital age, the advertising market is experiencing unprecedented growth, but with it comes a persistent shadow: ad fraud. This multi-billion dollar industry drains significant portions of advertising budgets annually, erodes trust in online channels, and distorts analytical data, leading to flawed strategic decisions. According to various sources, such as Statista, losses from ad fraud amount to tens of billions of dollars each year. Major players like Google Ads and Yandex.Direct (though less globally prominent, its principles apply similarly to other regional networks) invest colossal resources in developing and implementing sophisticated systems to combat fraudulent activity. They employ advanced machine learning algorithms, behavioral analysis, vast databases, and dedicated teams of highly skilled professionals.
However, despite these titanic efforts, ad fraud continues to thrive, evolving and adapting to new defense mechanisms. Why is it that even such technological giants cannot completely eradicate this problem? In this article, we will conduct a deep technical analysis of the reasons behind this paradox. We’ll examine not only the internal defense mechanisms of ad networks but also the fundamental challenges that hinder their full effectiveness, and suggest practical approaches for advertisers to fight for clean traffic.
The Anatomy of Ad Fraud: Who, What, and How
Before diving into the complexities of fighting fraud, it’s essential to understand its nature and primary types. Ad fraud is a deliberate fraudulent activity aimed at generating fake impressions, clicks, or conversions to illicitly profit from advertisers or corrupt their statistics.
Main Types of Ad Fraud:
- Bot Traffic: The most common type of fraud, where automated programs (bots) imitate human actions: clicks, views, and sometimes more complex behaviors. Bots can be relatively simple (e.g., scripts constantly clicking an ad) or extremely sophisticated, capable of bypassing basic CAPTCHAs and mimicking mouse movements.
- Click Farms: The use of real people, often from developing countries, who manually click on ads or perform other target actions. Although this is “live” traffic, it’s not targeted and brings no real value to the advertiser.
- Sophisticated Invalid Traffic (SIVT): These are advanced bots that use machine learning to mimic complex behavioral patterns of real users: page scrolling, cursor movements, form filling, viewing multiple pages on a site. Such bots are difficult to distinguish from real humans.
- Ad Injection: Malicious actors inject ads (often via malware, browser extensions, or internet service providers) onto web pages or into applications without the consent of the site owners. The advertiser pays for impressions that the user did not request and that are displayed in an uncontrolled environment.
- Domain Spoofing / Domain Misrepresentation: Presenting low-quality ad inventory (e.g., impressions on a junk site) as high-quality (e.g., impressions on a well-known news portal) by falsifying URLs in ad request calls.
- Ad Stacking: Placing multiple ad creatives on top of each other within a single ad unit. Only the top ad is visible to the user, but impressions are counted for all layers, including the hidden ones.
- Pixel Stuffing: Placing an ad unit within a user-invisible one-pixel (1×1) iframe or in an invisible part of the page. Impressions are counted, but the user never sees the ad.
- Conversion Fraud: Simulating target actions (registrations, app installations, subscriptions, purchases) to receive payouts based on CPA (Cost Per Action) or CPI (Cost Per Install) models. This can be done by bots or real people (e.g., in fraudulent affiliate programs).
- Chargeback Fraud: In the context of affiliate programs or e-commerce, when a fraudster makes a purchase and then disputes the payment, getting the product/service for free and causing losses to the advertiser.
Motivation and Economics of Fraud
Fraud is a highly profitable business with relatively low risk. Fraudsters constantly seek new ways to bypass defense mechanisms, and the potential profit motivates their continuous development. Estimates from HUMAN Security (formerly White Ops) indicate that fraudsters can achieve up to 1000% ROI on their investments, making the fight against them an endless battle.
Built-in Fraud Prevention Mechanisms in Google Ads and Yandex.Direct
Ad giants invest heavily in fraud prevention technologies. Their protection systems are based on a multi-layered approach, including both preventive measures and post-facto analysis.
1. Machine Learning and Artificial Intelligence (ML/AI)
ML and AI are at the core of modern fraud detection systems. They allow for the analysis of massive volumes of data in real-time and the identification of anomalies that would be impossible to detect manually.
- Behavioral Analysis: Algorithms analyze thousands of parameters related to user behavior. This includes:
- Click speed and sequence: Unnaturally fast or rhythmic clicks.
- Mouse movements/screen taps: Lack of natural randomness, straight lines, overly uniform movements.
- Time on page/time between actions: Abnormally short or long durations.
- Traffic source: Where the user came from, referrer information.
- Depth of view: Number of pages viewed, interaction with content.
- Uniqueness of IP address, User-Agent, cookie ID, device ID: Analysis of repetition and uniqueness of identifiers.
- Geographical location and language: Discrepancy between IP address and reported browser language or device settings.
- Screen resolution, OS version, browser: Comparison with typical patterns.
- Clustering and Segmentation: Identifying groups of suspicious IP addresses, devices, User-Agents, or behavioral patterns that may indicate coordinated botnet attacks or click farms.
- Predictive Modeling based on Historical Data: Using accumulated data on past fraudulent activities to build predictive models that help identify new, previously unknown fraud schemes. For example, if a specific IP range has historically generated abnormally high traffic without conversions, the system can automatically deprioritize or block it.
2. Network and Request-Level Filtering
- Blacklists: Extensive databases of known fraudulent IP addresses, IP ranges, proxy servers, VPN services, data centers, and User-Agents associated with fraud. These lists are constantly updated.
- Geolocation and Anomalies: Analysis of discrepancies between reported location (based on IP address) and other signals (e.g., browser language, device time zone). If clicks on an English ad come from IP addresses deep within China, it raises suspicion.
- Traceroute and Routing Analysis: Tracking the path of a request from source to server to identify suspicious proxy chains or atypical network routes.
- HTTP/HTTPS Header Analysis: Checking the uniqueness and correctness of headers sent by the browser or application. Some bots generate incorrect or suspicious headers.
3. Behavioral Analysis at the Campaign and Publisher Level
- CTR Anomalies: Unnaturally high or low CTR (Click-Through Rate) for specific ads, keywords, placements, or geographical regions can signal fraud. For example, a 50% CTR for a banner is a clear indicator.
- Conversion Discrepancies: A high percentage of clicks but an abnormally low percentage of conversions or their complete absence in subsequent funnel stages. If thousands of clicks yield no registrations or purchases, it raises questions.
- Publisher Data Analysis: Ad networks assess the quality of traffic provided by publishers based on their history, advertiser feedback, and internal metrics. Suspicious changes in traffic volume or quality can lead to manual review or automated sanctions.
4. Human Factor and Manual Moderation
- Advertiser Complaints: Reports and complaints from advertisers about suspicious traffic or ineffective campaigns are a crucial source of information for fraud fighting teams. These cases undergo manual review.
- Dedicated Fraud Teams: Google and Yandex employ large teams of experts who constantly research new fraud schemes, refine algorithms, conduct manual investigations, and respond to advertiser inquiries.
- Laboratory Research: Simulating fraud attacks in controlled environments to understand their mechanics and develop countermeasures.
Table 1: Key Metrics Used by Ad Networks for Fraud Detection
| Metric/Parameter | Example of Suspicious Value | Indication |
| CTR (Click-Through Rate) | >30% or <0.01% for display ads | Automated clicks, ad stacking, pixel stuffing, click farms |
| Average Session Duration | <10 seconds for most sessions, or abnormally long | Bots, uninterested traffic, behavioral mimicry |
| Bounce Rate | >90% for targeted traffic | Low-quality traffic, bots, setup errors |
| Geo-IP Discrepancies | Clicks from China on English ads targeted at the UK | VPNs, proxies, botnets |
| Recurring IP Addresses | Hundreds of clicks from one IP in a short period | Bots, click farms, network fraud |
| User-Agent | Incorrect, missing, or overly generic User-Agent | Bots, specialized fraud software |
| Pages per Session | Only one page viewed (for most sessions) | Uninterested traffic, bots |
| Clicks to Conversions Ratio | Thousands of clicks but 0 conversions | Click fraud, low-quality traffic, tracking issues |
Why These Measures Are Not Enough: Fundamental Challenges
Despite all the measures listed above, ad networks cannot completely solve the problem of ad fraud due to several fundamental reasons:
1. Adaptability and Evolution of Fraud: The Arms Race
This is perhaps the most significant reason. The fight against fraud is a continuous “arms race,” where each side constantly adapts to the other’s actions.
- Continuous Improvement of Fraud Technologies: Fraudsters invest in research and development no less than ad networks. They create increasingly sophisticated bots capable of:
- Mimicking Human Behavior: Modern bots can use machine learning and neural networks to learn from real user data. They imitate natural mouse movements, scrolling, delays, text input, viewing multiple pages, using different browsers and devices. Such bots are extremely difficult to distinguish from real users based on behavioral patterns alone.
- Bypassing CAPTCHAs and Multi-Factor Authentication: Services for solving CAPTCHAs (manual or automated) are used, as well as technologies to bypass MFA.
- Using Real Devices (Device Farms): Instead of purely software-based bots, farms of real smartphones or computers are used to run scripts mimicking human actions. This is virtually indistinguishable from real traffic.
- Distributed Attacks and Botnets: Fraudsters use thousands or millions of unique IP addresses belonging to infected home computers, IoT devices, proxy networks, or VPN services. This makes blocking by IP addresses or their ranges ineffective, as each click comes from a “clean” IP.
- Exploitation of “Clean” Traffic Sources: Fraudsters can hack legitimate websites, inject hidden ad blocks into them, or use them to generate fraudulent traffic.
2. Limited Data Access and “Blind Spots” of Ad Networks
Ad networks, even large ones like Google and Yandex, have certain limitations in data collection, creating “blind spots” for fraud detection.
- Limited Context Outside the Platform: Ad networks only see the portion of user interaction that occurs within their ecosystem or is directly related to clicking on an ad. They do not see the full picture:
- How users interact with other ad networks before or after clicking their ad.
- What browser extensions are installed on the user’s device (some of which may be malicious and inject ads).
- The user’s full journey on the advertiser’s website (deep behavioral analysis often requires access to web server logs or analytics data).
- The presence of specific malware on the user’s device that may generate fraudulent impressions/clicks.
- Data Privacy (GDPR, CCPA, ePrivacy Directive, etc.): Increasingly stringent data privacy laws limit the volume and type of information ad networks can collect about users. This, on one hand, protects users, but on the other, complicates the detection of sophisticated fraud that requires deep analysis of behavioral patterns and identifiers.
- Distrust and Lack of Full Data Exchange Between Market Players: Ad networks are competitors. This makes it difficult to create unified databases of fraudulent IP addresses, schemes, or identifiers. Each player fights fraud separately, giving fraudsters an advantage by allowing them to switch between platforms.
3. Difficulty in Identifying “Clean” Clicks and Balancing Interests
- Fine Line Between Non-Targeted Traffic and Fraud: It’s sometimes very difficult to distinguish low-quality but non-fraudulent traffic (e.g., accidental clicks, very low user interest, erroneous actions) from genuine fraud. Overly aggressive filtering can lead to legitimate traffic being cut off, which reduces ad network revenue and can cause dissatisfaction among publishers and advertisers.
- “Suspicion” vs. “Proof”: Ad network systems must be conservative enough in their blocking decisions to avoid mistakenly blocking a legitimate user or publisher. This means that a high level of confidence is required to deem something fraud, which gives fraudsters a window of opportunity.
- Conflict of Interest with Publishers: Ad networks earn revenue from displaying ads. The more traffic they can monetize, the higher their revenue. Overly aggressive filtering can lead to reduced traffic volumes for publishers, directly impacting their revenue and loyalty to the platform. This creates an internal conflict where a compromise must be found between traffic purity and monetization volume.
- False Positives: Even the most advanced AI systems can make mistakes. A legitimate advertiser or publisher mistakenly blocked results in reputational damage and financial losses. Therefore, systems are configured to minimize false positives, which sometimes means letting some real fraud through.
4. Human Factor and Social Engineering
Despite all technological advancements, humans remain a weak link.
- Click Farms: As mentioned, real people hired to mimic clicks are almost impossible to distinguish from real users at the automated system level if their behavior is plausible enough.
- Social Engineering and Deception: Fraudsters can use social engineering to gain access to advertiser or publisher accounts, or to create fake affiliate networks.
What Advertisers Can Do: Tools and Best Practices
Since ad networks cannot provide 100% protection, advertisers must actively participate in the fight for the quality of their traffic. This requires using third-party tools and implementing internal processes.
1. Anti-Fraud Solutions
Specialized platforms exist that offer deeper analysis and tools for fraud detection than the built-in systems of ad networks. Examples include: Clickfraud, BotGuard, Voluum (with Anti-Fraud module), AppsFlyer (for mobile fraud), Adjust (for mobile fraud).
These systems often offer:
- SIVT Detection: Advanced behavioral analysis that goes beyond the capabilities of ad networks.
- Device Fingerprinting: Creating unique identifiers for devices without using cookies, which helps identify recurring fraudulent traffic.
- Proxy/VPN Analysis: Deep inspection of IP addresses to determine if they belong to proxies, VPNs, data centers, or known botnets.
- Traffic Source Validation: Verifying the consistency between the declared traffic source and the actual one.
- Real-time Blocking: Some systems can block suspicious clicks or impressions before they are paid for.
Example of an Anti-Fraud Platform Usage (Conceptual):
Let’s say you use a third-party tracker integrated with your ad system and an anti-fraud platform.
- Set up Postback/API Integration:Ad System (Google Ads/Yandex.Direct) -> Your Tracker/Analytics -> Anti-Fraud Platform.Your tracker/analytics collects click and conversion data.
- Send Data to the Anti-Fraud Platform:Example URL for tracking clicks with parameter passing:
https://yourtracker.com/click?campaignid={campaignid}&adgroupid={adgroupid}&keyword={keyword}&source={source}&ip={ip}&user_agent={user_agent}&clickid={clickid}Here,yourtracker.comis your tracker. It then forwards this data to the Anti-Fraud system. - Analysis and Reporting: The Anti-Fraud platform analyzes this data, identifies fraud, and provides reports. It can recommend excluding suspicious IPs, placements, or even automatically block them via API.
- Example API Request for IP Blocking (conceptual, depends on the Anti-Fraud service): Python
import requests api_key = "YOUR_ANTI_FRAUD_API_KEY" block_ip_url = "https://antifraudservice.com/api/v1/block_ip" ip_to_block = "192.168.1.100" # IP identified as fraudulent headers = { "Authorization": f"Bearer {api_key}", "Content-Type": "application/json" } payload = { "ip_address": ip_to_block, "reason": "Suspected bot activity", "duration": "permanent" } response = requests.post(block_ip_url, headers=headers, json=payload) if response.status_code == 200: print(f"IP {ip_to_block} successfully blocked.") else: print(f"Failed to block IP. Status: {response.status_code}, Response: {response.text}")
2. Internal Monitoring and Analytics
- Deep Web Analytics Analysis (Google Analytics, Yandex.Metrica): Don’t limit yourself to ad network reports. Analyze user behavior on your site:
- Bounce Rate: An abnormally high bounce rate (over 80-90%) for specific traffic sources, keywords, or campaigns can indicate bots or non-targeted traffic.
- Time on Site and Pages per Session: Very short session times (<10-15 seconds) and viewing only one page.
- Geography and Language: Discrepancy between traffic geography and campaign targeting. For example, if you’re targeting London, but 30% of traffic comes from Asia.
- Technical Parameters: Use of outdated browsers, unusual screen resolutions, frequent session resets.
- Action Sequence: Lack of natural click sequences or mouse movements.
- Excluding IP Addresses: Regularly add suspicious IP addresses and ranges to exclusions in Google Analytics and Yandex.Metrica so they don’t skew your statistics.
- Using Custom Segments: Create user segments in your analytics to isolate and analyze suspicious traffic.
- Example segment in Google Analytics: “IP Address contains X OR IP Address contains Y” or “User Agent contains ‘bot’ OR ‘spider'”.
3. Campaign Setup for Fraud Minimization
- Precise Targeting: The more precise your targeting (geography, audience, time), the harder it is for fraudsters to generate “matching” traffic.
- Negative Keywords and Placement Exclusions: Regularly update negative keyword lists and exclude ineffective or suspicious placements (websites, apps) from ad display.
- In Google Ads: “Placements” report -> “Where ads showed”. Analyze placements with high CTR but low conversions or high bounce rates.
- In Yandex.Direct: “Placement Report”.
- Use of Remarketing Lists: Remarketing traffic is usually higher quality as it has already interacted with your site.
- Frequency Capping: Limit the number of times an ad is shown to a single user to reduce opportunities for fraud.
- Monitoring Anomalies in Ad Network Reports:
- Google Ads: “Reports” section -> “Predefined reports” -> “Basic” -> “Placements”. Look at the same metrics as in web analytics.
- Yandex.Direct: Use “Report Wizard” for deep analysis of conversions or clicks.
4. Lead and Conversion Verification
- Phone Verification: For inquiries or calls.
- Email Verification: Double opt-in for subscriptions.
- CRM Data Analysis: Compare data from ad networks with actual sales and lead quality in your CRM. If leads from certain traffic sources never convert into sales, it’s a reason for investigation.
- CRM Integration with Analytics: Set up end-to-end analytics to see which sources bring real customers, not just clicks.
Table 2: Comparison of Built-in and Third-Party Approaches to Fighting Fraud
| Criterion/Approach | Built-in Ad Network Mechanisms | Third-Party Anti-Fraud Platforms | Advertiser’s Internal Monitoring |
| Data Access | Limited to platform ecosystem | Broader, incl. device fingerprint, proxy data | Full access to advertiser’s site data |
| Analysis Depth | Basic to medium, focus on volume | High, SIVT, behavioral analysis | Depends on analyst skill and setup |
| Configuration Flexibility | Limited by platform interface | High, customizable rules, API | Full, but requires manual work |
| Real-time Action | Yes, automatic filtering | Can be, via API blocking | Often post-facto, manual blocking |
| Cost | Included in advertising cost | Additional expense (subscription) | Costs for specialist time and tools |
| Advantages | Automation, broad coverage, scalability | Deep detection, independence, control | Full control, business verification, end-to-end analytics |
| Disadvantages | “Blind spots”, conflict of interest, fraud adaptability | Added complexity, cost, requires integration | Requires expertise, time-consuming, human factor |
Conclusion: A Collaborative Fight for a Clean Ad Landscape
The problem of ad fraud is a complex, constantly evolving challenge that cannot be fully resolved by ad networks alone. Their built-in mechanisms, powered by advanced machine learning algorithms, are powerful tools, but they face fundamental limitations: the adaptability of fraudsters, data limitations, and inherent conflicts of interest.
For advertisers, this means one thing: the responsibility for traffic quality also lies with them. Utilizing third-party anti-fraud solutions, performing deep web analytics, meticulously configuring ad campaigns, and, most importantly, continuously monitoring and verifying conversions are not just “best practices” but a vital necessity. Only through collaborative efforts — continuous development of defense technologies by ad networks and a proactive stance by advertisers — can losses from fraud be minimized, and a more transparent and effective advertising landscape be built. This is an investment that pays off not only in saved budgets but also in reliable analytics, enabling truly informed business decisions.
List of Sources for Material Preparation:
- Statista: Ad fraud cost worldwide. Available at: https://www.statista.com/statistics/1231627/ad-fraud-cost-worldwide/ (accessed July 23, 2025).
- HUMAN Security (formerly White Ops): 2023 Bot & Fraud Report. Available at: https://www.humansecurity.com/press-releases/human-releases-2023-bot-fraud-report-revealing-20-of-web-traffic-is-bad-bots (accessed July 23, 2025).
- Why Attribution Tools by Themselves are not Enough to Combat Mobile Ad Fraud – https://www.mmaglobal.com/news/why-attribution-tools-themselves-are-not-enough-combat-mobile-ad-fraud-0
- Ad Fraud, The Forever Menace? And How Can We Defeat It? – https://etailasia.wbresearch.com/blog/ad-fraud-the-forever-menace-and-how-can-we-defeat-it